Website value calculator & SEO Checker => cso.com.au
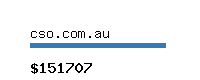
SEO report with information and free domain appraisal for cso.com.au. It is a domain hosted in . Its server is hosted on IP 146.75.62.165. The domain is ranked at the number 49377 as a world ranking of web pages. According to estimated data we have access to potential gains of this site are 1264 dollars per month. In annual terms, the domain cso.com.au could be earning more than 15171 dollars. If someone wanted to buy the domain a good selling price would be 151707 dollars.
These data are estimated and can not be taken as 100 % real. Only give an estimate of profits depending on the subject and the traffic generated by cso.com.au . The estimated number of unique visitors accessing cso.com.au is 11046. Thus the total number of people who visit this page per month would be 331383 people.
Domain Authority
SEO Score
☰ Report Resume
- SEO score
- Speed
- Page Load Time
- Current Ip of the domain: 146.75.62.165
- Charset of page: UTF-8
- Total Keywords: 908
- Total Links: Anchor textTypeLinkClose Adfollowjavascript:unhide("superadunit");cso onlinefollow/United Statesfollow/ASEANfollow/asean/Australiafollow/au/Indiafollow/in/United Kingdomfollow/uk/follow/insider/Government-wide DNS security strengthens Australia’s cyberdefencefollow/article/3637769/government-wide-dns-security-strengthens-australia-s-cyberdefence.htmlHow Jemena is preparing for Australia’s coming critical infrastructure cybersecurity obligationsfollow/article/3635551/how-jemena-is-preparing-for-australia-s-coming-critical-infrastructure-cybersecurity-obligations.htmlWhy Australian property and real estate CISOs need to be on high alertfollow/article/3634971/why-australian-property-and-real-estate-cisos-need-to-be-on-high-alert.htmlAustralia’s physical-security specialists looking to take on information securityfollow/article/3634455/australia-s-physical-security-specialists-looking-to-take-on-information-security.htmlMore Insiderfollow/insider/Sign Outfollowjavascript://Sign Infollowjavascript://Registerfollowjavascript://follow#searchfollowfollowfollow#searchfollow/about/learn-about-insider.htmlSign Outfollowjavascript://Sign Infollowjavascript://Registerfollowjavascript://followLearn Morefollowhttps://www.idginsiderpro.com/subscribePoorly educated boards mean less cybersecurity funding for ANZ CISOsfollow/article/3634394/poorly-educated-boards-mean-less-cybersecurity-funding-for-anz-cisos.html10 top API security testing toolsfollow/article/3632856/10-top-api-security-testing-tools.htmlHow to mitigate the Microsoft Office zero-day attackfollow/article/3633881/how-to-mitigate-the-microsoft-office-zero-day-attack.htmlThe new math of cybersecurity valuefollow/article/3632947/the-new-math-of-cybersecurity-value.htmlNEW FROM IDG Learn Morefollowhttps://www.idginsiderpro.com/subscribefollow/about/learn-about-insider.htmlhere.follow/insiderSign Outfollowjavascript://Sign Infollowjavascript://Registerfollowjavascript://About Usfollow/about/about.htmlContactfollow/about/contactus.htmlReprintsfollow/about/contactus.html#reprintsPrivacy Policyfollow/about/privacy.htmlCookie Policyfollow/about/cookie-policy.htmlMember Preferencesfollow/about/member-preferences.htmlAdvertisingnofollowhttps://www.idg.com/our-brands/cso/IDG Careersnofollowhttps://www.idg.com/work-here/Ad Choicesfollow/about/adchoices.htmlE-commerce Linksfollow/about/affiliates.htmlCalifornia: Do Not Sell My Personal Infofollow/about/ccpa.htmlnofollowhttp://www.linkedin.com/company/csoonlinenofollowhttps://twitter.com/csoonlinenofollowhttps://www.facebook.com/CSOonlinefollowfollowGovernment-wide DNS security strengthens Australia’s cyberdefencefollow/article/3637769/government-wide-dns-security-strengthens-australia-s-cyberdefence.html6 zero trust myths and misconceptionsfollow/article/3634395/6-zero-trust-myths-and-misconceptions.htmlCybersecurity breach of Australian banks is ‘inevitable’, Reserve Bank warnsfollow/article/3636990/cybersecurity-breach-of-australian-banks-is-inevitable-reserve-bank-warns.htmlfollow/article/3637769/government-wide-dns-security-strengthens-australia-s-cyberdefence.htmlGovernment-wide DNS security strengthens Australia’s cyberdefencefollow/article/3637769/government-wide-dns-security-strengthens-australia-s-cyberdefence.htmlHow Jemena is preparing for Australia’s coming critical infrastructurefollow/article/3635551/how-jemena-is-preparing-for-australia-s-coming-critical-infrastructure-cybersecurity-obligations.htmlView Allfollow/au/insiderfollow/article/3013033/security-recruiter-directory.htmlSecurity Recruiter Directoryfollow/article/3013033/security-recruiter-directory.htmlWhat is Magecart? How this hacker group steals payment card datafollow/article/3400381/what-is-magecart-how-this-hacker-group-steals-payment-card-data.htmlView Allfollow/au/featurefollow/article/3232355/saml-explained-how-this-open-standard-enables-single-sign-on.htmlSAML explained: How this open standard enables single sign onfollow/article/3232355/saml-explained-how-this-open-standard-enables-single-sign-on.htmlHow to check for Active Directory Certificate Services misconfigurationsfollow/article/3623270/how-to-check-for-active-directory-certificate-services-misconfigurations.htmlView Allfollow/au/howtofollow/video/111179/reviewing-software-risks-on-your-windows-networkReviewing software risks on your Windows networkfollow/video/111179/reviewing-software-risks-on-your-windows-networkHow to mitigate the Microsoft MSHTML remote code execution zero-dayfollow/video/110999/how-to-mitigate-the-microsoft-mshtml-remote-code-execution-zero-dayView Allfollow/au/video/series/8607/windows-security-tipsfollow/article/3013033/security-recruiter-directory.htmlSecurity Recruiter Directoryfollow/article/3013033/security-recruiter-directory.htmlfollowfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3013033%2Fsecurity-recruiter-directory.html&via=csoonline&text=Security+Recruiter+Directoryfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3013033%2Fsecurity-recruiter-directory.htmlnofollowmailto:?Subject=Security Recruiter Directory&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3013033%2Fsecurity-recruiter-directory.htmlfollow/article/3638108/decline-in-ransomware-claims-could-spark-change-for-cyber-insurance.htmlDecline in ransomware claims could spark change for cyber insurancefollow/article/3638108/decline-in-ransomware-claims-could-spark-change-for-cyber-insurance.htmlMichael Hillfollow/author/Michael-Hill/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3638108%2Fdecline-in-ransomware-claims-could-spark-change-for-cyber-insurance.html&via=csoonline&text=Decline+in+ransomware+claims+could+spark+change+for+cyber+insurancefollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3638108%2Fdecline-in-ransomware-claims-could-spark-change-for-cyber-insurance.htmlnofollowmailto:?Subject=Decline in ransomware claims could spark change for cyber insurance&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3638108%2Fdecline-in-ransomware-claims-could-spark-change-for-cyber-insurance.htmlfollow/article/3637124/detecting-anomalies-with-tls-fingerprints-could-pinpoint-supply-chain-compromises.htmlDetecting anomalies with TLS fingerprints could pinpoint supply chain compromisesfollow/article/3637124/detecting-anomalies-with-tls-fingerprints-could-pinpoint-supply-chain-compromises.htmlLucian Constantinfollow/author/Lucian-Constantin/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637124%2Fdetecting-anomalies-with-tls-fingerprints-could-pinpoint-supply-chain-compromises.html&via=csoonline&text=Detecting+anomalies+with+TLS+fingerprints+could+pinpoint+supply+chainfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637124%2Fdetecting-anomalies-with-tls-fingerprints-could-pinpoint-supply-chain-compromises.htmlnofollowmailto:?Subject=Detecting anomalies with TLS fingerprints could pinpoint supply chain compromises&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637124%2Fdetecting-anomalies-with-tls-fingerprints-could-pinpoint-supply-chain-compromises.htmlfollow/article/3400381/what-is-magecart-how-this-hacker-group-steals-payment-card-data.htmlWhat is Magecart? How this hacker group steals payment card datafollow/article/3400381/what-is-magecart-how-this-hacker-group-steals-payment-card-data.htmlDavid Stromfollow/author/David-Strom/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3400381%2Fwhat-is-magecart-how-this-hacker-group-steals-payment-card-data.html&via=csoonline&text=What+is+Magecart%3F+How+this+hacker+group+steals+payment+card+datafollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3400381%2Fwhat-is-magecart-how-this-hacker-group-steals-payment-card-data.htmlnofollowmailto:?Subject=What is Magecart? How this hacker group steals payment card data&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3400381%2Fwhat-is-magecart-how-this-hacker-group-steals-payment-card-data.htmlfollow/article/3637769/government-wide-dns-security-strengthens-australia-s-cyberdefence.htmlGovernment-wide DNS security strengthens Australia’s cyberdefencefollow/article/3637769/government-wide-dns-security-strengthens-australia-s-cyberdefence.htmlDavid Brauefollow/author/David-Braue/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637769%2Fgovernment-wide-dns-security-strengthens-australia-s-cyberdefence.html&via=csoonline&text=Government-wide+DNS+security+strengthens+Australia%E2%80%99s+cyberdefencefollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637769%2Fgovernment-wide-dns-security-strengthens-australia-s-cyberdefence.htmlnofollowmailto:?Subject=Government-wide DNS security strengthens Australia’s cyberdefence&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637769%2Fgovernment-wide-dns-security-strengthens-australia-s-cyberdefence.htmlfollow/au/newsletters/signup.htmlGet the best of CSO delivered to your inbox. Sign up for our free newslettersfollow/au/newsletters/signup.htmlSubscribefollow/au/newsletters/signup.htmlfollow/article/3637113/new-windows-browser-security-options-and-guidance-what-you-need-to-know.htmlNew Windows browser security options and guidance: What you need to knowfollow/article/3637113/new-windows-browser-security-options-and-guidance-what-you-need-to-know.htmlSusan Bradleyfollow/author/Susan-Bradley/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637113%2Fnew-windows-browser-security-options-and-guidance-what-you-need-to-know.html&via=csoonline&text=New+Windows+browser+security+options+and+guidance%3A+What+you+need+to+knowfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637113%2Fnew-windows-browser-security-options-and-guidance-what-you-need-to-know.htmlnofollowmailto:?Subject=New Windows browser security options and guidance: What you need to know&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637113%2Fnew-windows-browser-security-options-and-guidance-what-you-need-to-know.htmlfollow/article/3637058/isc2-pilots-new-entry-level-cybersecurity-certification-to-tackle-workforce-shortages.html(ISC)2 pilots new entry-level cybersecurity certification to tackle workforce shortagesfollow/article/3637058/isc2-pilots-new-entry-level-cybersecurity-certification-to-tackle-workforce-shortages.htmlMichael Hillfollow/author/Michael-Hill/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637058%2Fisc2-pilots-new-entry-level-cybersecurity-certification-to-tackle-workforce-shortages.html&via=csoonline&text=%28ISC%292+pilots+new+entry-level+cybersecurity+certification+to+tackle+workforcefollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637058%2Fisc2-pilots-new-entry-level-cybersecurity-certification-to-tackle-workforce-shortages.htmlnofollowmailto:?Subject=(ISC)2 pilots new entry-level cybersecurity certification to tackle workforce shortages&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637058%2Fisc2-pilots-new-entry-level-cybersecurity-certification-to-tackle-workforce-shortages.htmlfollow/article/3635894/ssrf-attacks-explained-and-how-to-defend-against-them.htmlSSRF attacks explained and how to defend against themfollow/article/3635894/ssrf-attacks-explained-and-how-to-defend-against-them.htmlAx Sharmafollow/author/Ax-Sharma/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3635894%2Fssrf-attacks-explained-and-how-to-defend-against-them.html&via=csoonline&text=SSRF+attacks+explained+and+how+to+defend+against+themfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3635894%2Fssrf-attacks-explained-and-how-to-defend-against-them.htmlnofollowmailto:?Subject=SSRF attacks explained and how to defend against them&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3635894%2Fssrf-attacks-explained-and-how-to-defend-against-them.htmlfollow/article/3636449/8-top-multifactor-authentication-products-and-how-to-choose-an-mfa-solution.html8 top multifactor authentication products and how to choose an MFA solutionfollow/article/3636449/8-top-multifactor-authentication-products-and-how-to-choose-an-mfa-solution.htmlTim Ferrillfollow/author/Tim-Ferrill/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636449%2F8-top-multifactor-authentication-products-and-how-to-choose-an-mfa-solution.html&via=csoonline&text=8+top+multifactor+authentication+products+and+how+to+choose+an+MFA+solutionfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636449%2F8-top-multifactor-authentication-products-and-how-to-choose-an-mfa-solution.htmlnofollowmailto:?Subject=8 top multifactor authentication products and how to choose an MFA solution&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636449%2F8-top-multifactor-authentication-products-and-how-to-choose-an-mfa-solution.htmlfollow/article/3637118/white-house-international-ransomware-initiative-outlines-hopes-and-challenges.htmlWhite House international ransomware initiative outlines hopes and challengesfollow/article/3637118/white-house-international-ransomware-initiative-outlines-hopes-and-challenges.htmlChristopher Burgessfollow/author/Christopher-Burgess/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637118%2Fwhite-house-international-ransomware-initiative-outlines-hopes-and-challenges.html&via=csoonline&text=White+House+international+ransomware+initiative+outlines+hopes+and+challengesfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637118%2Fwhite-house-international-ransomware-initiative-outlines-hopes-and-challenges.htmlnofollowmailto:?Subject=White House international ransomware initiative outlines hopes and challenges&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3637118%2Fwhite-house-international-ransomware-initiative-outlines-hopes-and-challenges.htmlPopular Resourcesfollow/resourcesView Allfollow/resourcesfollow/resources/226204/the-modern-workplace-a-new-normal-for-today-s-businessesThe Modern Workplace – A New Normal For Today’s Businessesfollow/resources/226204/the-modern-workplace-a-new-normal-for-today-s-businessesfollow/resources/225999/2021-cloud-protection-trends-report2021 Cloud Protection Trends Reportfollow/resources/225999/2021-cloud-protection-trends-reportfollow/resources/225904/a-new-network-for-a-new-era-how-to-build-resilience-into-your-connected-infrastructureA New Network For A New Era – How to Build Resilience Into Your Connected Infrastructurefollow/resources/225904/a-new-network-for-a-new-era-how-to-build-resilience-into-your-connected-infrastructurefollow/resources/225801/making-the-move-to-modern-igaMaking the Move to Modern IGAfollow/resources/225801/making-the-move-to-modern-igafollow/article/3635849/microsofts-very-bad-year-for-security-a-timeline.htmlMicrosoft"s very bad year for security: A timelinefollow/article/3635849/microsofts-very-bad-year-for-security-a-timeline.htmlMichael Hillfollow/author/Michael-Hill/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3635849%2Fmicrosofts-very-bad-year-for-security-a-timeline.html&via=csoonline&text=Microsoft%27s+very+bad+year+for+security%3A+A+timelinefollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3635849%2Fmicrosofts-very-bad-year-for-security-a-timeline.htmlnofollowmailto:?Subject=Microsoft"s very bad year for security: A timeline&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3635849%2Fmicrosofts-very-bad-year-for-security-a-timeline.htmlfollow/article/3634395/6-zero-trust-myths-and-misconceptions.html6 zero trust myths and misconceptionsfollow/article/3634395/6-zero-trust-myths-and-misconceptions.htmlNeal Weinbergfollow/author/Neal-Weinberg/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3634395%2F6-zero-trust-myths-and-misconceptions.html&via=csoonline&text=6+zero+trust+myths+and+misconceptionsfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3634395%2F6-zero-trust-myths-and-misconceptions.htmlnofollowmailto:?Subject=6 zero trust myths and misconceptions&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3634395%2F6-zero-trust-myths-and-misconceptions.htmlfollow/article/3636990/cybersecurity-breach-of-australian-banks-is-inevitable-reserve-bank-warns.htmlCybersecurity breach of Australian banks is ‘inevitable’, Reserve Bank warnsfollow/article/3636990/cybersecurity-breach-of-australian-banks-is-inevitable-reserve-bank-warns.htmlDavid Brauefollow/author/David-Braue/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636990%2Fcybersecurity-breach-of-australian-banks-is-inevitable-reserve-bank-warns.html&via=csoonline&text=Cybersecurity+breach+of+Australian+banks+is+%E2%80%98inevitable%E2%80%99%2C+Reserve+Bank+warnsfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636990%2Fcybersecurity-breach-of-australian-banks-is-inevitable-reserve-bank-warns.htmlnofollowmailto:?Subject=Cybersecurity breach of Australian banks is ‘inevitable’, Reserve Bank warns&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636990%2Fcybersecurity-breach-of-australian-banks-is-inevitable-reserve-bank-warns.htmlfollow/article/3614764/top-cybersecurity-manda-deals-for-2021.htmlTop cybersecurity M&A deals for 2021follow/article/3614764/top-cybersecurity-manda-deals-for-2021.htmlCSO stafffollow/author/CSO-staff/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3614764%2Ftop-cybersecurity-manda-deals-for-2021.html&via=csoonline&text=Top+cybersecurity+M%26A+deals+for+2021followhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3614764%2Ftop-cybersecurity-manda-deals-for-2021.htmlnofollowmailto:?Subject=Top cybersecurity M&A deals for 2021&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3614764%2Ftop-cybersecurity-manda-deals-for-2021.htmlfollow/article/3636456/how-shape-shifting-threat-actors-complicate-attack-attribution.htmlHow shape-shifting threat actors complicate attack attributionfollow/article/3636456/how-shape-shifting-threat-actors-complicate-attack-attribution.htmlCynthia Brumfieldfollow/author/Cynthia-Brumfield/followfollowhttps://twitter.com/intent/tweet?url=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636456%2Fhow-shape-shifting-threat-actors-complicate-attack-attribution.html&via=csoonline&text=How+shape-shifting+threat+actors+complicate+attack+attributionfollowhttps://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636456%2Fhow-shape-shifting-threat-actors-complicate-attack-attribution.htmlnofollowmailto:?Subject=How shape-shifting threat actors complicate attack attribution&Body=Check%20out%20this%20article%20from%20CSO Online%3A%20https%3A%2F%2Fwww.csoonline.com%2Farticle%2F3636456%2Fhow-shape-shifting-threat-actors-complicate-attack-attribution.htmlfollowhttps://www.cio.com/native-link/boundless-agility/?utm_source=home&utm_medium=sponsoredpromo&utm_campaign=intelFeatured Sponsor Intel Competitive Advantage with a Modern Data Center that Delivers Boundless Agilityfollowhttps://www.cio.com/native-link/boundless-agility/?utm_source=home&utm_medium=sponsoredpromo&utm_campaign=intelfollow/article/3634457/trust-transformation-creating-a-robust-security-culture-built-for-tomorrow-s-it-leaders.htmlSponsored by Okta Trust Transformation – Creating a Robust Security Culture Built for Tomorrow’sfollow/article/3634457/trust-transformation-creating-a-robust-security-culture-built-for-tomorrow-s-it-leaders.htmlfollow/article/3632393/zero-trust-a-mindset-change-needed-to-secure-the-next-digital-decade.htmlSponsored by Thales Zero Trust: a mindset change needed to secure the next digital decadefollow/article/3632393/zero-trust-a-mindset-change-needed-to-secure-the-next-digital-decade.htmlfollow/article/3625235/how-to-secure-the-modern-customer-experience.htmlSponsored by Okta How to Secure the Modern Customer Experiencefollow/article/3625235/how-to-secure-the-modern-customer-experience.htmlCSO Onlinefollow/nofollowhttp://www.linkedin.com/company/csoonlinenofollowhttps://twitter.com/csoonlinenofollowhttps://www.facebook.com/CSOonlineAbout Usfollow/about/about.htmlContactfollow/about/contactus.htmlReprintsfollow/about/contactus.html#reprintsPrivacy Policyfollow/about/privacy.htmlCookie Policyfollow/about/cookie-policy.htmlMember Preferencesfollow/about/member-preferences.htmlAdvertisingnofollowhttps://www.idg.com/our-brands/cso/IDG Careersnofollowhttps://www.idg.com/work-here/Ad Choicesfollow/about/adchoices.htmlE-commerce Linksfollow/about/affiliates.htmlCalifornia: Do Not Sell My Personal Infofollow/about/ccpa.htmlCopyrightfollow/about/tos.htmlCIOnofollowhttps://www.cio.comComputerworldnofollowhttps://www.computerworld.comCSO Onlinenofollowhttps://www.csoonline.comInfoWorldnofollowhttps://www.infoworld.comNetwork Worldnofollowhttps://www.networkworld.com
- Social signals
- Title: 96 characters.
- Description: 235 characters.
- Domain Authority
- Monthly pages viewed: 331383
- Estimated worth: 151707 dollars
We have developed a useful service for retrieve WhoIs information. "Whois" is a term that begins from the early days of the Internet, based on Unix operating system and university networks. On the Unix console, the command "whois" tries to determine the identity of the domain's registrant.
It is a means for Internet users to query various types of information such as IP addresses, user data and also domain data.
✦ SEO Report
Title / Meta tags
CSO | Security news, features and analysis about prevention, protection and business innovation.
CSO offers the latest information and best practices on business continuity and data protection, best practices for prevention of social engineering scams, malware and breaches, and tips and advice abut security careers and leadership.
Image Analysis
A right example for an HTML image tag:
<img src="prettyimage.jpg" alt="image description" title="image tooltip"/>
For SEO performance, you must write an alternative text. The alternative text must describe the image's content. Also, the alt tag is used for blind people. Their browsers tell them all about the description of the image.
Heading
Content Analysis
Code Analysis
We have not found hyphens (-) or underscores (_) in your URL. Google and expert domainers do not recommend buying domains with hyphens or underscores.
When a visitor came to your website you can not fail. The user wants your page to load in a second. You know that it is difficult sometimes to display content in the first second but if the user has to wait too much time you can lose that user. If your page is too slow, you will lose a lot of web traffic. Your project URL load time is ms, it is class speed. This speed not fine and need to be improved. It is over the average. Our Speed analyzer has shown that www.cso.com.au is as follows:
A huge portion of visitors to your website are usually in rush and nobody is fond of waiting too much before your website loads its content. If your website is slow, you will lose a lot of visitors. Your homepage load time is ms is class speed. This speed not fine and need to be improved. It is over the average. Our Speed analyzer has shown that www.cso.com.au is as follows:
Speed:
Page Load Time: ms
The Analytics id for cso.com.au is 300704
.An IP address is a string of numbers used to make devices accessible for communication.
To display an HTML page correctly, a web browser must know which character set to use.
The charset change for every language set of characters like English, Chinese or Russian.
The links are an important part of the web.
The links help us to navigate between pages.
The number of words is a crucial metric of the website.
The websites need a large quantity of text to explain the content of the site
Last visited